Home | Glossary | Resources | Help | Contact Us | Course Map
Archival Notice
This is an archive page that is no longer being updated. It may contain outdated information and links may no longer function as originally intended.
Storage Options
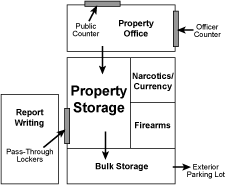
How evidence is secured in a laboratory is based on the physical plant and the organizational structure of the laboratory.
Physical plant factors include
- overall size of the laboratory building,
- amount of space allocated for storage,
- whether the building was originally designed or retrofitted as a laboratory.
Organizational structure factors include
- number of disciplines performed in the laboratory,
- staffing level of the laboratory,
- the number of disciplines performed by individual examiners.
Storage of evidence for each forensic discipline or groups of disciplines is handled in either a centralized or decentralized system. Centrally stored evidence is checked out and in by the examiner as needed. In comparison, a decentralized system allows for more immediate access to evidence because it is stored in the examination area.
Physical Integrity of Evidence
Whether centralized or decentralized within the laboratory, all evidence storage facilities must maintain the physical integrity of the evidence, to include provision for the following:
- Basic environmental controls for temperature and humidity
- Alarm systems for unauthorized entry (motion, vibration, and sound detection)
- Video coverage of sensitive areas
- Fire alarm and sprinkler systems
- Refrigeration for certain types of evidence
- Protection from floods
- Protection from pests
- Storage located under a secure roof, particularly in storm-threatened areas
- Fume hood, as appropriate to preserve evidence
Controlled Access
The goal in controlling access to evidence is to serve both the needs of the examiner and the need for security. This involves planning, developing protocols, and educating all staff and visitors. When these elements move from paper to practice, the result is layered security, which appropriately limits access to certain areas of the laboratory and to evidence items. Electronic keys are most effective and convenient when integrated into employee identification badges.
Common features of controlled access:
- Limited access to laboratory space, excluding public reception areas
- Evidence reception area access for law enforcement personnel only with suitable identification
- Requirement for an identifiable laboratory point of contact to escort authorized visitors (investigators, prosecutors, etc.) to laboratory operating spaces
- Guest badges/ID for all escorted visitors
- Electronic and/or traditional key access for laboratory employees coded to:
- laboratory common areas,
- relevant discipline workspace, such as decentralized evidence storage facilities, and
- individual examiner evidence lockers within that space.
Regardless of the system employed to control access, provision should be made to ensure that unusual or emergency situations can be addressed, such as:
- Access by fire and rescue personnel. This is often accomplished by posting information for a contact person on the exterior of the building.
- Access to all evidence storage areas by laboratory managers in the event of temporary or permanent absence of examiners. This can be addressed by ensuring access to all appropriate spaces whether by limited issue master keys or broad-access electronic keys.
Biometric Systems
More costly options include advanced biometric methods for access control, such as any or a combination of the following:
- Iris/retinal scans
- Facial recognition systems
- Fingerprint (dermal ridge) recognition
High Security
Certain types of physical evidence require special attention simply due to their nature. In many forensic laboratories, the examiner at the hub of the chain of custody will be required to follow additional procedures for the protection of the examiner and for the security of the evidence. Frequently, this involves a storage protocol that uses a separate storage facility accessed only by the examiner and the laboratory director (or designee). They would be required to access the evidence at the same time, recording each access in a logbook.
While these measures may appear excessive at first glance, the precautions are prudent for an examiner with chain-of-custody responsibility.
If a firearm/toolmark examiner is the hub of the chain of custody for firearm/toolmark evidence only , the following physical evidence examples may require high-security measures:
- Collectable firearms of high value, such as historic or rare firearms (property of historic figures, assassination firearms, etc.)
- Evidence firearms in current high-profile cases subject to intense media interest
- Sensitive or classified items with a requirement for limited access on a need-to-know basis
If a firearm/toolmark examiner is the hub of the chain of custody for all forms of evidence in a submission, these additional examples would also apply:
- Cash, negotiable bonds, or any other financial instruments that could easily be converted to personal use
- Drug evidence
- Jewelry, precious metals, rare or gold coins, gemstones, or any other items of high intrinsic value
Additional Online Courses
- What Every First Responding Officer Should Know About DNA Evidence
- Collecting DNA Evidence at Property Crime Scenes
- DNA – A Prosecutor’s Practice Notebook
- Crime Scene and DNA Basics
- Laboratory Safety Programs
- DNA Amplification
- Population Genetics and Statistics
- Non-STR DNA Markers: SNPs, Y-STRs, LCN and mtDNA
- Firearms Examiner Training
- Forensic DNA Education for Law Enforcement Decisionmakers
- What Every Investigator and Evidence Technician Should Know About DNA Evidence
- Principles of Forensic DNA for Officers of the Court
- Law 101: Legal Guide for the Forensic Expert
- Laboratory Orientation and Testing of Body Fluids and Tissues
- DNA Extraction and Quantitation
- STR Data Analysis and Interpretation
- Communication Skills, Report Writing, and Courtroom Testimony
- Español for Law Enforcement
- Amplified DNA Product Separation for Forensic Analysts