Mass public attacks, whether personally or ideologically motivated, cause much concern and fear. Nonetheless, you can often take actions to prevent, defend against, and respond to mass attacks. A recent NIJ-funded[1] research project analyzed over 600 mass attack plots, hundreds of articles and resources, and dozens of expert interviews to develop the Mass Attacks Defense Toolkit,[2] an online educational toolkit with strategies, guidance, and links to additional resources. Access the toolkit.
Here are five critical points resulting from this research project:
1. We can proactively prevent many mass attacks. Public reporting prevented almost two-thirds of the foiled plots highlighted in the toolkit.
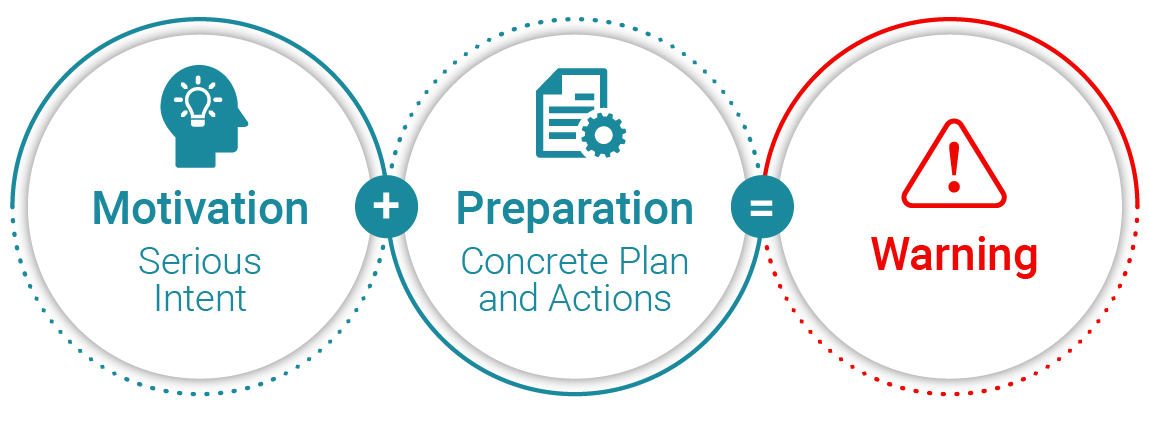
Look for warning signs, such as the following:
- Motivation
- Inspired by previous attacks.
- Desire to fulfill an extremist cause (especially upon expulsion from a group/organization for being too violent).
- Desire to fulfill an extremist cause while believing there is no other choice but to attack due to perceived danger or threat.
- Preparation
- Creates written plan.
- Attempts to recruit others.
- Seeks information on how to maximize impact.
- Coordinates with known violent extremists.
- Seeks arsenals of weapons, ammunitions, and gear (except for benign uses, such as sporting or hunting).
- Travels frequently (for training or targeting).
- Probes or breaches potential sites.
Exhibit 1: The Importance of Noticing Warning Signs
2. Communities need multidisciplinary, multi-partner teams to follow up and assess warning signs and determine what to do next.
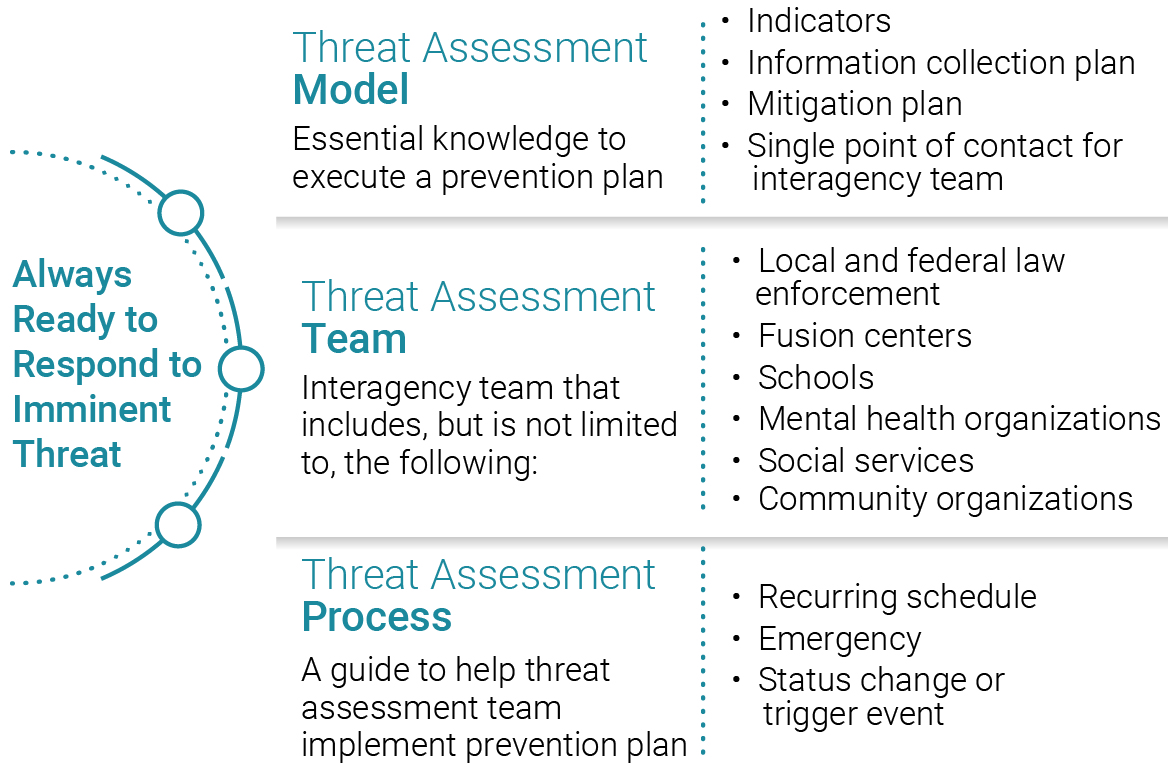
Every case needs a single lead or responsible partner to direct the necessary follow up. Exhibit 2 shows the core elements of a typical threat assessment model, team, and process.
Threat assessment is not just about the likelihood of an attack; it also requires determining the next steps to take with the subject, most of which may be outside the criminal justice system. Critical components include documenting next steps and check-in points to ensure follow-through.
Exhibit 2: Core Elements of a Typical Threat Assessment, Model, Team, and Process
3. Adequate preparation reduces casualties in the critical beginning stages of an attack before responders arrive to the scene.
From a site-security management perspective:
- Prevent shooters from surprising a crowd at close range and cutting off methods of escape.
- Create buffer zones (distance).
- Facilitate opportunities for movement of crowds away from potential shooters (to emergency exits or known secured rooms).
- Place physical barriers (walls, locked doors, secure windows) between potential shooters and crowds.
From a potential victim perspective, employ the strategy of Run, Hide, and Fight:[3]
- Be prepared to Run if you can safely escape the scene.
- It may be safer to Hide in a secure location rather than trying to safely escape the scene.
- Fight only when you cannot escape or hide; use distractions, employ anything that can serve as a weapon, and move at angles to the shooter.
4. An effective joint response to a mass attack requires planning and training that includes everyone who will be involved in a response.
Effective attack responses include coordination between law enforcement, fire, and emergency medical services, as well as hospitals, victim service providers, site security managers, and site personnel. For this to occur, leaders need to provide adequate planning and training support and direction.
The Mass Attacks Defense Toolkit provides numerous skills and resources to assist joint responders with planning and training. For example, all partners should learn the Incident Command System[4] and National Incident Command System,[5] as command and communications during an attack are paramount. Planning and training must cover communications — including common radio frequencies or groups — as well as radio discipline to keep channels from being overloaded. Planning and training must also cover dispatching and traffic control to ensure that vehicles and personnel don’t clog the scene and hamper parts of the response (e.g., not leaving room for ambulances).
5. The recovery plan must include planning and training for the aftermath.
Actions in the immediate aftermath of the attack include locating and apprehending attackers (where applicable), investigating attackers and potential co-conspirators, and providing access to mental health and emotional support, such as establishing family assistance centers and providing for victim welfare.
- Near-term actions include mental health and emotional support for victims, survivors, and responders, along with debriefing sessions to record critical information regarding the response and review the available resources for victims.
- Long-term actions for first responders include providing ongoing mental health and emotional support for survivors and responders, monitoring the recovery process of victims, and engaging in recognition and learning — such as awards for acts of valor, ceremonies for victims and heroes, memorial and commemoration events, and after-action reports.