Introduction
A widespread technology that allows people to connect with anyone, anywhere, has created concerns for corrections officials. The use of inexpensive, disposable cell phones has changed the age-old cat-and-mouse game of controlling whom incarcerated persons communicate with in the outside world and is creating serious problems for public safety officials.
In the 1990s, cellular phones were larger and heavier and had audio capabilities only. Today they are lightweight, can be thinner than a match- book, and can send both audio and data, including written messages and streaming video. Although these advances are welcome in society in general, they have had a negative impact on the law enforcement community, as criminals have taken advantage of cellular technology to conduct illegal activities.
Cell Phones Are a Widespread Problem
The issue of cellular phone use by criminals, especially those incarcerated in prison or jail, gained national attention when a person incarcerated on death row used a cell phone to threaten a Texas senator. In Nevada, prison officials fired a dental assistant for helping an incarcerated person get a cell phone to plan a successful escape. In New York, an incarcerated person used a cell phone to orchestrate an attempted escape while on a medical transfer. In Tennessee, prison officials banned jars of peanut butter after learning that an incarcerated person accused in the shooting death of a guard had used a jar to hide the cell phone he used to coordinate his escape. Incarcerated persons have also used cell phones to harass and threaten their victims. In Texas, courts have convicted more than a dozen corrections officers in recent years for accepting bribes in exchange for cell phones or phone parts.
Cell Phones as Contraband
The number of contraband cell phones being confiscated is also noteworthy. For example, in California, correctional officers seized 1,331 cell phones in the first six months of 2008. Corrections officials in other states have also reported finding hundreds of cell phones.
Corrections officials have spent millions of dollars to outfit prisons and jails with metal detectors, but the detectors do little to stem the flow of cell phones from the outside. Some cell phone parts are made of plastic and go undetected.
Shutting Down Cell Phones
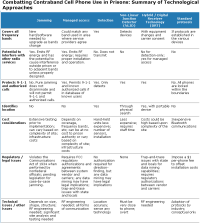
Blocking cell phone service involves using technologies to stop the transmission or reception of other radio signals. In some cases, blocking signals can be tuned to leave specific frequencies open, which would allow for communication among corrections personnel, or they can block almost all signals. The power of the blocking signal determines how large an area is affected. The area could be as small as a cell block or large enough to cover an entire prison. Blocking systems can cost as little as $1,000, but more powerful systems can cost tens of thousands of dollars.
Another technology allows for spoofing cell phone signals. Spoofing involves intercepting selected cell phone transmissions and preventing them from reaching the intended recipient. Spoofing uses sophisticated software and is possible without the active participation of the cell phone network providers. A drawback to selective blocking and spoofing is the potential for incarcerated persons to use approved cell phones that belong to staff members.
A report by the National Telecommunications and Information Administration — developed in collaboration with NIJ the Federal Communications Commission and Federal Bureau of Prisons — discusses the characteristics and capabilities of the various technologies and the potential interference effects that they may have on authorized radio services, including commercial wireless, public safety communications and 9-1-1 calls. [1]
Technologies discussed in the report include:
- A jamming device transmits on the same radio frequencies as the cell phone, disrupts the communication link between the phone and the cell phone base station, and essentially renders the hand-held device unusable until such time as the jamming stops. Learn more about jamming (pdf, 58 pages).
- Managed access systems intercept calls in order to prevent incarcerated persons from accessing carrier networks. The cell signal is not blocked by a jamming signal, but rather, is captured (or re-routed) and prevented from reaching other network base stations, thereby preventing the completion of the call. Learn more about managed access systems (pdf, 58 pages).
See also: - Detection is the process of locating, tracking, and identifying various sources of radio transmissions — in this case, cell phone signals from prisons. Learn more about detection technologies (pdf, 58 pages) and see also A Market Survey on Contraband Detection Technologies.
- Standardized protocols rely on "sets of instructions" communicating with the hand-held device by essentially locking the device and making it unusable. Learn more about standardized protocols (pdf, 58 pages).
- Hybrid systems use a combination of both managed access and detection techniques to locate and control contraband cell phone use. Learn more about hybrid systems.
- Non-Linear Junction Detectors (NLJDs) are hand-held devices that require staff to physically search prison cells for contraband phones. Learn more about non-linear junction detectors (pdf, 58 pages).
Federal Government Rules
The Communications Act of 1934 and the Telecommunications Act of 1996 prohibit the operation of cell-phone-jamming equipment by any person, including state and local officials. Specifically, Section 333 of the Communications Act prohibits willful or malicious interference with any licensed or authorized radio communications equipment or with radio equipment operated by the United States government. In addition, the Act prohibits the manufacture, importation, marketing, sale or operation of devices deliberately designed to jam or disrupt wireless communications.
Legislation in Congress titled the Safe Prisons Communications Act of 2009 would let prisons and jails use cell-phone-jamming technology.
Countering the Problem
As they await legislative relief from the problem, corrections officials are using various technologies that detect and find cell phones. Both high-technology and low-technology approaches are being tested and used. Several agencies have installed sensors that detect and find cell phones when in use. One such device tested in a Pennsylvania prison signaled cell phone location to within four cells on two tiers. Some sensors can even detect cell phones that are turned off, but they only work when in close proximity to a phone, cost between $15,000 and $20,000, and require trained staff. Others use new detectors that can identify nonmetallic objects to conduct searches. For smaller facilities, the use of specially formulated paints and coatings that block radio frequency signals may help.
Some correctional institutions use specially trained dogs to sniff out hidden cell phones. These efforts have not been rigorously evaluated. Dog training can cost tens of thousands of dollars. Dogs must be close to the phone, and anecdotal evidence suggests that the phone must be left in the same place for a considerable time to be found.
Most of these solutions are expensive and labor intensive. Each would benefit from a thorough evaluation.